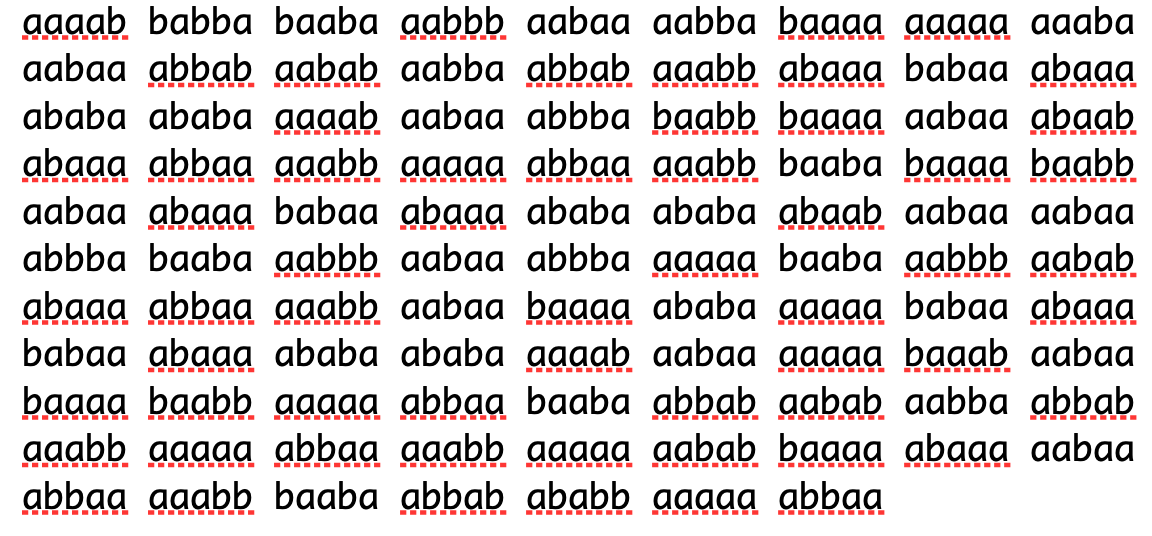Difference between revisions of "AY Honors/Cryptography/Answer Key"
| Line 314: | Line 314: | ||
<!-- 8. Choose a cipher to encrypt a favorite Bible text and let another person decrypt it. Be sure to give that person the type of cipher and the key used. --> | <!-- 8. Choose a cipher to encrypt a favorite Bible text and let another person decrypt it. Be sure to give that person the type of cipher and the key used. --> | ||
| − | You have plenty of choices for this one. Here is an example of using a columnar transposition cipher (with a key) to encode our message. In this form of cipher, we write our plain text in a grid horizontally, and write our cipher text by reading the columns vertically. But the twist is the key. Before writing our text, we write the key word across our grid. This determines how many rows we will have. The rows are then written as the cipher text based on the alphabetical order of the letters in the key word - so the first column isn't necessarily the first column we will write. If there are two of the same letter in the key word, the first appearance comes first in numbering the columns. | + | You have plenty of choices for this one. |
| + | |||
| + | Here is an example of using a columnar transposition cipher (with a key) to encode our message. In this form of cipher, we write our plain text in a grid horizontally, and write our cipher text by reading the columns vertically. But the twist is the key. Before writing our text, we write the key word across our grid. This determines how many rows we will have. The rows are then written as the cipher text based on the alphabetical order of the letters in the key word - so the first column isn't necessarily the first column we will write. If there are two of the same letter in the key word, the first appearance comes first in numbering the columns. | ||
So here is the way to encrypt using this method. Our plain text comes from the book of Psalm. Here we have converted the numbers to words so we do not need to worry about having numbers mixed with out letters. | So here is the way to encrypt using this method. Our plain text comes from the book of Psalm. Here we have converted the numbers to words so we do not need to worry about having numbers mixed with out letters. | ||
| Line 320: | Line 322: | ||
[[File:Plain Text Psalm to encode.png|frame|center]] | [[File:Plain Text Psalm to encode.png|frame|center]] | ||
| − | Our keyword is SHEPHARD. | + | Our keyword is SHEPHARD. Yes, it is spelled like a person's name, not the job with sheep. Using similar sounding words can add to the complexity if someone overhears the key word. The keyword should be sent (or pre-arranged) separately from the cipher text. Perhaps you can use steganography to hide the key word. So, our key, shephard, has 8 letters, so we will have 8 columns in our grid. When we encode, we will begin with the column beneath the letter "A," then the column beneath the letter "d," then "e," then the first "H," then the second "H" and so on. So here is the verse written out in our grid. |
[[File:Cipher psalm.png|frame|center]] | [[File:Cipher psalm.png|frame|center]] | ||
Revision as of 13:42, 11 June 2025
1
Cryptography is the science or process of encoding and decoding messages to allow more secure transfer of information.
2
2a
Codes use symbols to replace the original message. These may include images, numbers, colors, etc. In many codes, the entire word can be represented by a symbol or another word.
For example, if we see a traffic light, each color represents a word or phrase, with a specific meaning: red=stop, amber=caution, green=go. The color denotes a word, and is thus a code. At sea, ships may use flags and pennants as part of the International Code of Signals, each flag representing a letter, number, word, or phrase.
In wartime and in secret government communications, code words may be used to obfuscate the actual meaning. During World War II, for example, the U.S. Navy used code words to represent locations or activities, so if the message was intercepted, the enemy would not know what or where they were talking about.
For example, the word "BALSA" in a message meant "Midway Island," "WOODBANK" meant "Paris, France," and "RANCID" translated to "Greenland."
2b
A Cipher encrypts a message at the level of individual or small groups of letters, rather than replacing entire words. It is created (and solved) using an algorithm. A simple classic cipher, for example, is the Caesar cipher, where the alphabet is shifted a certain number of spaces to encode and decode the message. The example below is a Caesar cipher with a key of 3 (ie each letter is shifted 3 places). The algorithm could be written as (P)+X=(C), where "P" means the plain text letter, and "C" means the new cipher text letter, and "X" is the number of spaces to shift the letter. A 3 shift Caesar cipher, as below, adds 23 places (26 letters in the alphabet -3 shifted spaces) to get us our encoding, but we "subtract" three letters from the encoded message to solve for the original.
Using this cipher, we could encode the word "Ranger" as OXKDBO, the word "Voyager" as SLVXDBO
Another simple classic cipher is the Atbash cipher, where the code is the alphabet in reverse.
Using this cipher, we could encode the word "Companion" as xlnkzmrlm, the word "Guide" as tfrwv
Ciphers can be even more complex (and often are, particularly when using machines and computers). The Enigma machine of World War II used several mechanical elements to encode via a polyalphabetic cipher, meaning that in the enciphered text, a single letter may have different unencrypted meanings, based on where it was and how the algorithm encoded it.
2c
Steganography is the process of hiding data/information inside other data, for example hiding textual information in an image file, subtly changing fonts, or using invisible ink.
2d
Plain Text refers to the unencrypted information prior to encoding
2e
A key is the information necessary to encrypt and decrypt a particular message. In a Caesar cipher, it is the number of letters to shift.
2f
A public key is part of a two-key encryption/decryption model, where one key is private, and another is publicly available. Public Key Cryptography is also called Asymmetric Cryptography, and is a way of transmitting secure messages via the internet/email, where even if intercepted the message cannot be decrypted.
2g
A one way function is a model of encrypting information where it is relatively easy to convert the data one way, but much more difficult to reverse the process. In some computer applications, this one way function results in a hash value, allowing secure storage of sensitive information or passwords. If someone breaks into the database, they can only recover the hash value, which obscures the original information.
3
3a
Transposition is a classic cipher that moves the position of letters in a word or phrase, rather than replacing them. At its simplest, this could involve just shifting things around (Hello Friend might be encoded as Olleh Dneirf). Other forms include a rail fence ciphers as shown below, which write the words in a zig-zag pattern and then encode across the rows.
A two-line rail fence cipher, to encode "Pathfinders Strong." Once entered into the blocks, we would then send the encoded message as "PTFNESTOGAHIDRSRN"
A three-line rail fence cipher, to encode "pathfinders strong." Once entered into the blocks, we would send the encoded message as "pfetgahidrsrntnso"
3b
A traditional Polybius Square is a 5X5 grid with the alphabet filling in the square (English alphabet needs a larger square, or combines two letters, such as I and J or U and V of C and K). Each square is then given a 2 digit code as per its column and row number.
Using the square above, we would encode the word "Pathfinder" as: "53 11 44 32 12 42 33 41 51 24"
3c
In a square cipher, the letters are placed in a grid, and encoded against another grid. A common square grid is a four square grid, made up (as the name implies) of four 5X5 grids. The upper left and lower right are a regular alphabet, the upper right and lower left may have a code word (in this case Pathfinder Strong is the code word - the code word is written in the squares first, then the grid is finished with the rest of the alphabet).
To encode a message, it is first broken into two-letter segments. So pathfinder becomes pa th fi nd er (if there were an odd number of letters, you would use an x to fill the final pair). The first letter of the pair is found in the upper left grid, the second of the pair in the lower right. To encode, move along the row from the first letter to pair up with the column of the second letter. Then for the second letter, move along its row to align with the column of the first letter.
In the image here, we have also color coded to see. So PA = BN, TH = QC, FI = EG, ND = KR, ER = AU. We would then send the encoded message (Pathfinder) as BNQCEGKRAU
3d
A substitution cipher is a simple cipher, where each letter/number is replaced by an alternate letter/number/symbol. The characters are changed for the encoded message, but not the order of characters. Morse Code can be considered a substitution cipher, as each letter is replaced with a unique set of dashes and dots, which allowed the message to be sent across telegraph lines by sending longer (dash) or shorter (dot) pulses of electricity.
3e
In a polyalphabetic cipher, the substituted letter is determined both by the key and the placement in a word. So it may be that every third letter, the cipher shifts, or there is a different cipher for first letter, second letter, third letter, etc. In this style, the encoded message letters may represent different letters in the unencoded message, as different ciphers are used for different positions. It is more complicated to decode than a simple substitution cipher.
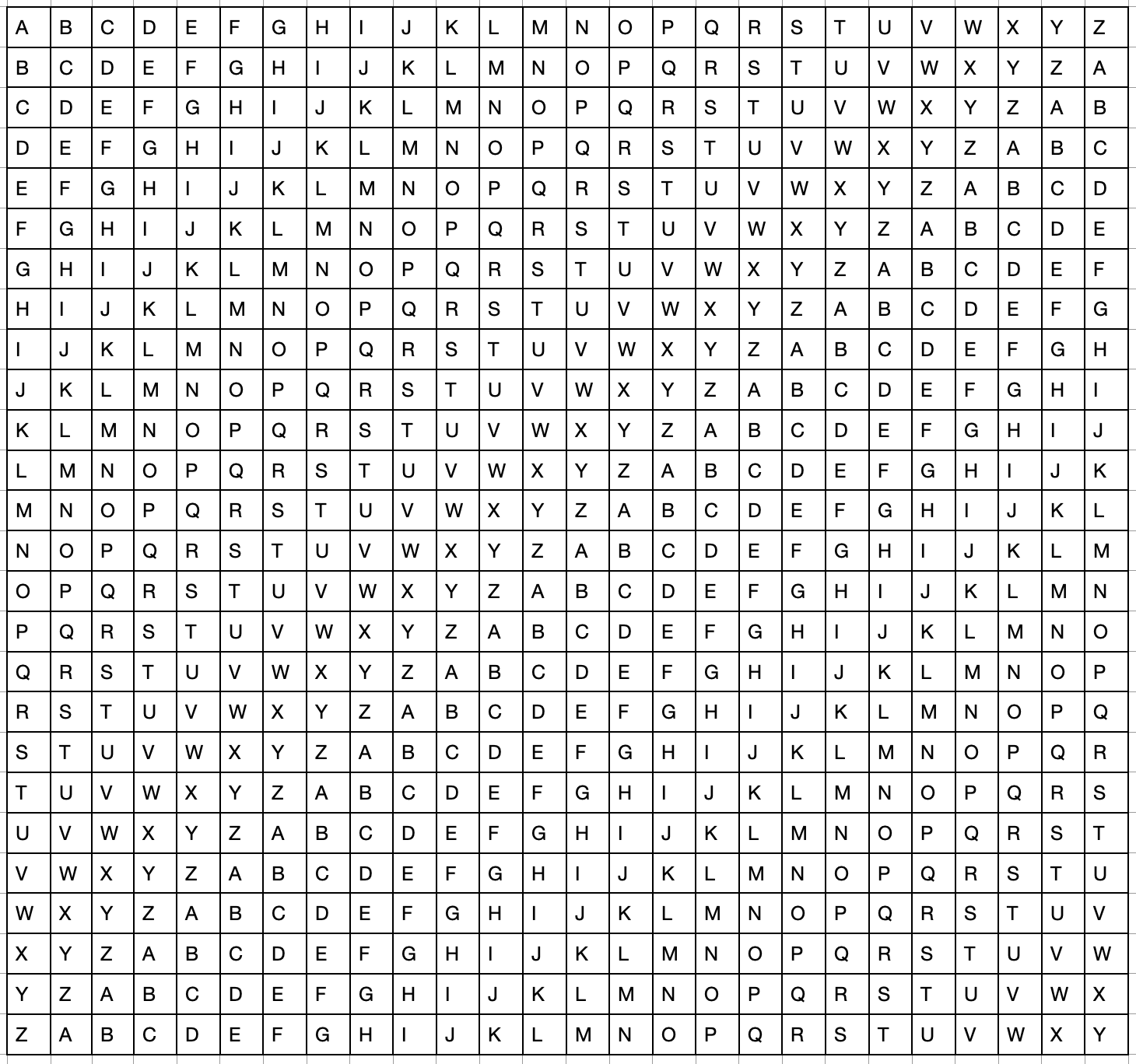
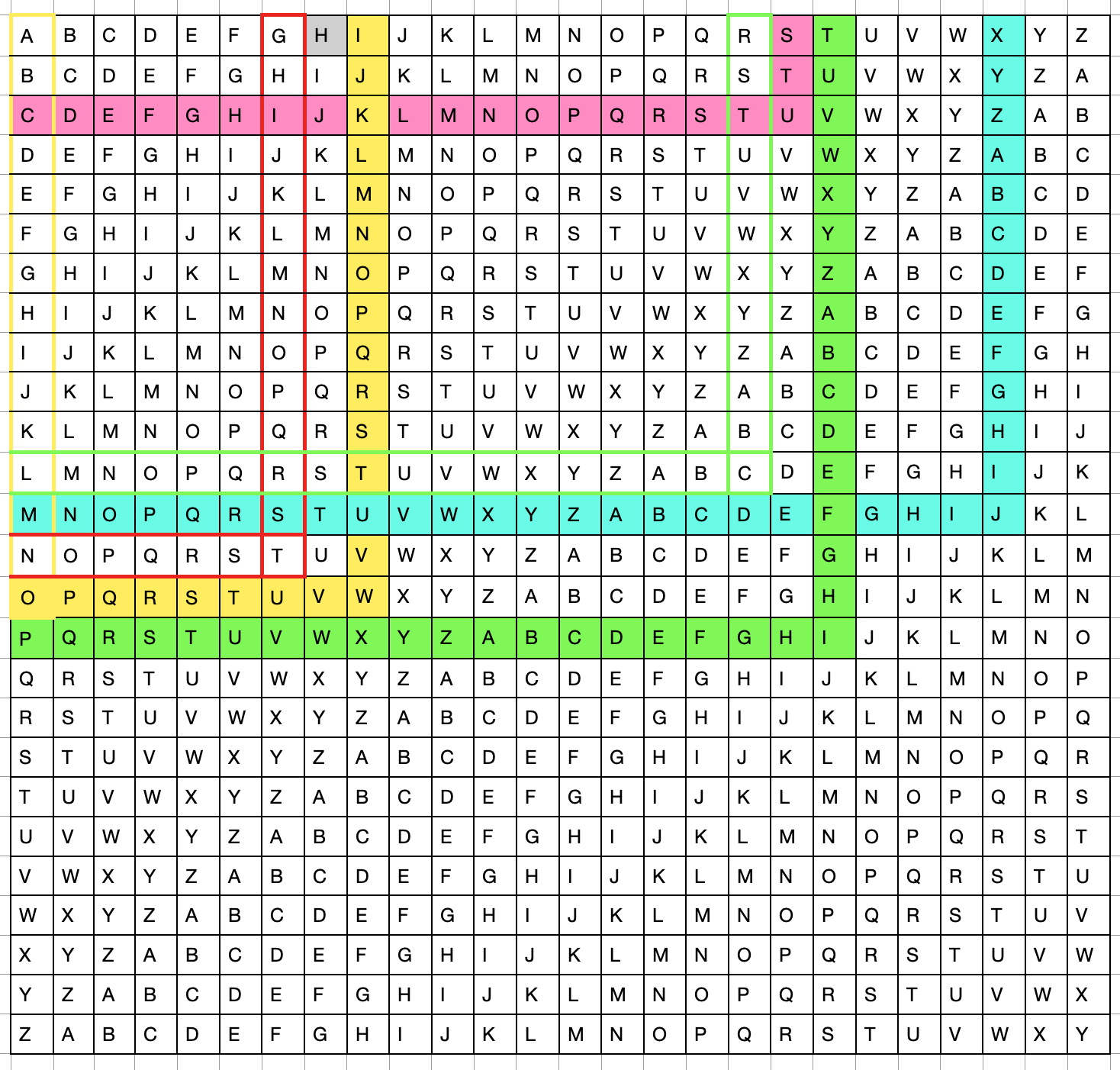
One well known polyalphabetic cipher is the Vigenere cipher, which uses a full alphabet grid (see below).
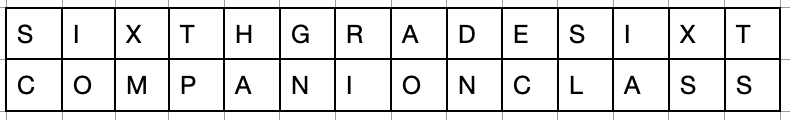
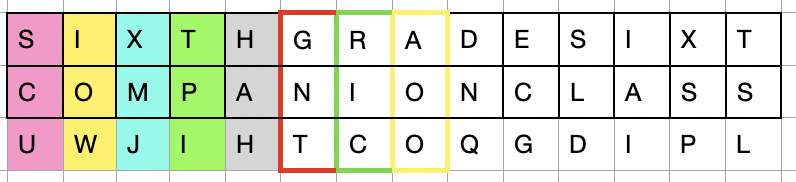
The message is encoded using a key phrase. The key phrase, repeated as necessary, is aligned above the unencoded text message, and each encoded replacement letter is found by the intersection of the key phrase letter column and the unencoded text letter row. In this case, we will use the key phrase "Sixth grade" and encode the message "Companion Class". We would align these atop one another, for example
To encode, we find the letter at the intersection of S and C, which is U. The next letter is encoded by finding the intersection of I and O, which is W. Once done, our message is encoded as UWJIHTCOQGDIPL
4
5
6
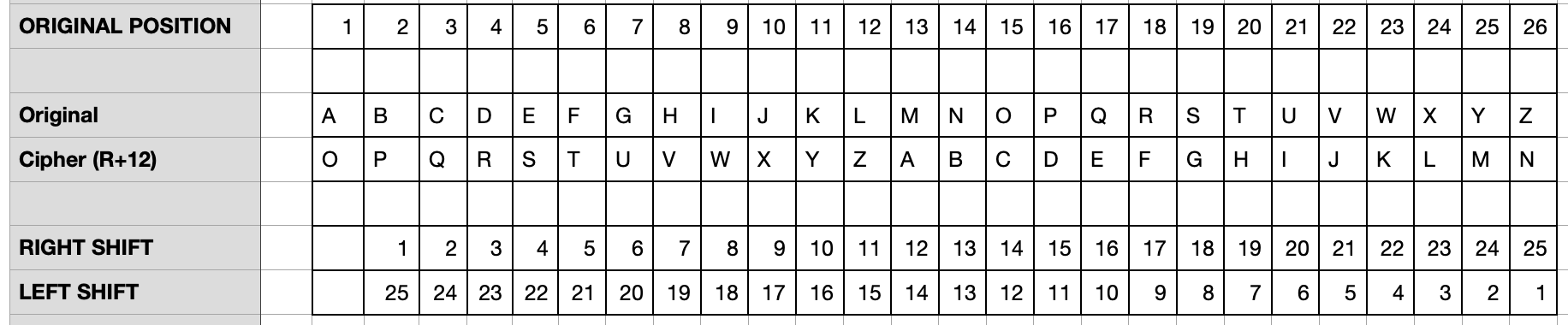
The Caesar cipher is a relatively simple cipher, with the coded text just shifting the letter a certain number of spaces left or right along the alphabet. If we have 26 letters in the alphabet, it means we can shift the alphabet 25 different ways right and 25 different ways left. A "right +2" Caesar cipher would move each letter two spaces to the right, so "A" would be encoded as "C," "B" would be "D" and so on, until "Y" wrapped around to "A" and "Z" wrapped around to be encoded as "B."
Here is a right +12 Caesar cipher (12 for the number of disciples). You can use a code phrase or some other way to signify the shift (though Caesar ciphers are relatively simple to break using brute force approaches and basic logic of language).
To use this, we first lay out our plain text
Now we encode the letters using our right +12 Caesar cipher
Finally, we remove our plain text, and can send the encoded text instead.
7
There are many online tools to embed messages in images using ‘least significant bit’ (LSB) steganography, which changes one character in the encoding of the colors for pixels. This is nearly invisible to the human eye, but can be decoded by machine. Changing a file by saving it somewhere else, or in a different format, however, may compromise the message. Information can also be hidden in video files, music files, and other digital media.
But one doesn't always need a computer to hide messages in plain sight. This has been done for centuries, by hand. Steganography is hiding a message in plain sight. One simple way to do this is to write the message in invisible ink, such as lemon juice. When the ink dries, it cannot be seen on the paper until treated (with lemon juice, that means exposing it to heat). If you write the message over an already printed paper, it is even more hidden, as those intercepting the message will think the plain text is the message when in fact the real message is hidden underneath and waits to be revealed.
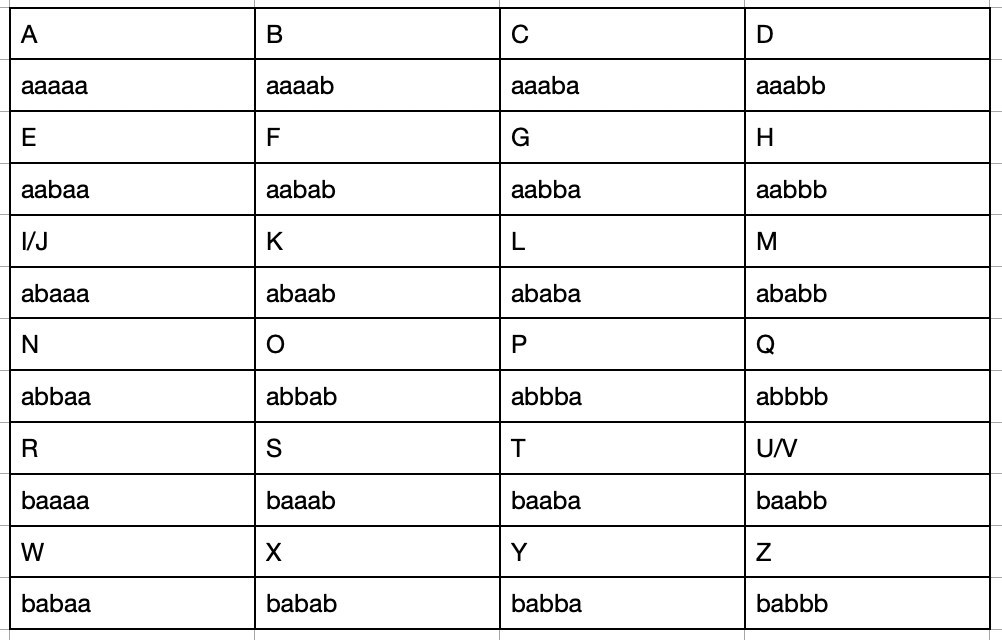
For a time-consuming but clever text based steganography, we can use Bacon's cipher to encode the Pathfinder Pledge. Bacon's cipher first replaces each letter with a five-letter a-b key (similar to binary, but using a and b rather than 0 and 1). Then, the message is written by using a different font or other clue for each a or b mapped against a piece of concealment text. It doesn't matter what the text is, so long as when it is written, one can break it into blocks of five letters, and see which letter represents an a or a b. Those five character a-b blocks then remap against the original cipher, revealing the original text.
Using Bacon's cipher, we can convert the Pathfinder Pledge to the following string of five-character a-b blocks. So we converted By (the first word of the pledge) into aaaab babba, and continue with the whole Pledge, ignoring spaces and punctuation.
Now we need our concealment text. The encrypted text is 485 characters long, so we need at least that much text. For this exercise, we have a selection from The Pathfinder Story, which, with its citation, is exactly 485 characters. We will hide the a-b encrypted text within this concealment text.
Now we take our concealment text, remove all of the punctuation and spaces, and break it into five character blocks, so we can map it against the cipher.
We can then map this set of five character text blocks against our cipher text so we know what characters to slightly alter to encode our message in plain sight.
For this version, we then take all of the letters that map against an "a" in the cipher text and leave them as 14 point font, while all the letters that map against a "b" in the cipher text are converted to 13 point font. It is a little noticeable, but not immediately obvious in the text that we have a hidden code.
To make it easier to see, here is some of the text with the 13 point font letters in red. We would not send it this way, but this may help you see how the encoding works in the concealment message.
To decrypt, we reverse the process. We first break our text into five character blocks, so we will be able to write out the cifer text. Here, we are using red to showcase which characters were in the 13 point font, while we leave the 14 point font characters in black.
Next, we convert the coded concealment text into a-b blocks. In this case, red (13 point font) letters are converted to "b," black (14 point font) characters are converted to "a."
Finally, we take the cipher text (the a-b blocks) and convert them to letters, giving us our hidden message.
The clever thing about Bacon's cipher, despite the long process, is that done right, it is almost impossible to tell that there is even a hidden message. By hiding the message in plain sight, others are less likely to think it is a message, and thus wont even work to break the cipher.
8
You have plenty of choices for this one.
Here is an example of using a columnar transposition cipher (with a key) to encode our message. In this form of cipher, we write our plain text in a grid horizontally, and write our cipher text by reading the columns vertically. But the twist is the key. Before writing our text, we write the key word across our grid. This determines how many rows we will have. The rows are then written as the cipher text based on the alphabetical order of the letters in the key word - so the first column isn't necessarily the first column we will write. If there are two of the same letter in the key word, the first appearance comes first in numbering the columns.
So here is the way to encrypt using this method. Our plain text comes from the book of Psalm. Here we have converted the numbers to words so we do not need to worry about having numbers mixed with out letters.
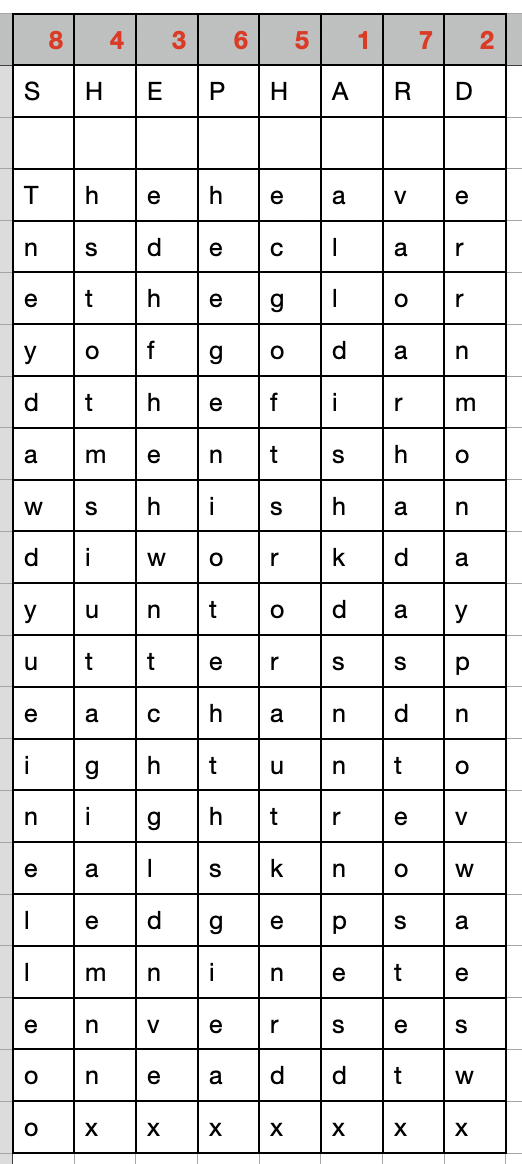
Our keyword is SHEPHARD. Yes, it is spelled like a person's name, not the job with sheep. Using similar sounding words can add to the complexity if someone overhears the key word. The keyword should be sent (or pre-arranged) separately from the cipher text. Perhaps you can use steganography to hide the key word. So, our key, shephard, has 8 letters, so we will have 8 columns in our grid. When we encode, we will begin with the column beneath the letter "A," then the column beneath the letter "d," then "e," then the first "H," then the second "H" and so on. So here is the verse written out in our grid.
Now we write out the coded message, starting with the column under "a," and so on.
Finally, we break it up (this time in groups of 5, but use whatever you want so long as it isnt the original number of columns)
To decode, we would take the key word, make a grid, count the total number of characters in the encoded message and divide by the number of columns in our table to determine how many rows we need. Then we begin writing the cipher text vertically in the table, beginning with the "A" column and so on. Once complete, we read/write it out horizontally across the rows to recover our original text.
9