Difference between revisions of "AY Honors/Computers/Answer Key"
m (W126jep moved page AY Honors/Computer/Answer Key to AY Honor Computers Answer Key without leaving a redirect: Part of translatable page "AY Honors/Computer/Answer Key") |
m |
||
| Line 217: | Line 217: | ||
<noinclude><translate><!--T:63--> | <noinclude><translate><!--T:63--> | ||
</noinclude> | </noinclude> | ||
| − | The A/C power that feeds most businesses and households is subject to all kinds of disturbances that can disrupt or damage a computer. Lightning strikes can induce large currents in | + | The A/C power that feeds most businesses and households is subject to all kinds of disturbances that can disrupt or damage a computer. Lightning strikes can induce large currents in powerlines, and these translate into "surge" voltages. The increased voltage can easily damage a computer. Most often, this affects its power supply module. A surge protector is designed to absorb these voltage surges, preventing damage to the computer. |
<noinclude></translate></noinclude> | <noinclude></translate></noinclude> | ||
{{CloseReq}} <!-- 7c --> | {{CloseReq}} <!-- 7c --> | ||
Revision as of 17:39, 27 July 2021
1
1a
1b
1c
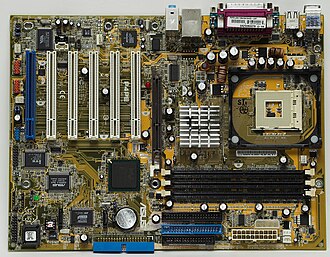
The mother board is located inside the main unit and contains the core circuitry of the computer, including the CPU. It also contains "slots" that other circuit cards such can be plugged into to add extra functions to the computer, such as a modem, networking, video acceleration, or a television tuner. The functions provided by these add-on cards (or daughter cards) are often absorbed into the motherboard as new technology is introduced. Modems, networking, sound, graphics, hard drive controllers, and USB adapters are examples of technology introduced as add-on cards, but now commonly found on the motherboard.
1d
1e
An external drive is a storage device that is connected to a computer via a USB (or other) port. The drive itself remains outside the computer. The advantage of an external drive is that it is easier to install and it can be moved from one computer to another. This feature can be used for physically transporting large amounts of data between computers, or securing the data in an off-site location.
1f
An internal drive is a storage device that is installed inside the computer. The advantage of an internal drive is that it takes up less space and is generally more reliable than an external drive.
1g
USB stands for Universal Serial Bus. It is a convenient method of interfacing many different devices to a computer. USB devices include cameras, printers, flash memory drives, external hard drives, music players, and many others. USB ports are located on the back, front, or both sides of a computer, and sometimes even on computer monitors. A USB device is simply plugged into the port, and the computer recognizes the device and prepares it for use.
1h
An optical drive is a device which reads and optionally writes data to optical storage media such as CD-ROMS and DVDs.
1i
An input device is any device through which data can be provided to a computer. Input devices include, the mouse, keyboard, network card, storage devices, cameras, microphones. bar code reader (like at grocery store), iris scanner, thumb print reader, video camera, touch screen, pin pad, card readers, near field communication (bluetooth), security sensors, RFID reader, tap and go for credit cards, motion sensors, light sensors.
1j
1k
1l
A printer is a device for capturing the output of a computer on paper.
1m
A mouse is a device that is used by human operators to control a computer. It can be used to move a cursor on a screen, highlight data on the screen, "drag and drop" files from one folder to another, control the action in a computer game, and manipulate data in many other ways.
1n
Modem stands for Modulator/Demodulator, and it a hardware device which allows computers to communicate with one another over a telephone line (or some other audio channel). A network card serves the same function except that it connects to a computer network (such as ethernet) and is much, much faster than a modem. Modems are used for "dial-up" internet connections, and network cards are used for "broadband" internet connections.
1o
A digital camera is a device which digitally captures and stores an image in the form of a photograph. The photograph can then be transferred to a computer where it can be stored, transmitted to other computers, or digitally manipulated.
1p
A scanner is a device which is used to digitize a two-dimensional image, such as a printed photograph, a page from a book, or a store receipt. 3D scanners are now becoming common.
2
CD's, CDR's, and DVD's are all forms of optical media, and as such, must be protected from scratches. They are fairly impervious to water, and in fact can be cleaned with it (just be sure to completely dry them off before trying to use them). Store them in protective cases, envelopes, or some other container designed to store them.
Flash/USB drives are incredibly durable and can take a lot of punishment. But that doesn't mean they should be abused. Though they are tough, they can still be crushed or snapped. Do not open the casing, as this will expose the internal circuitry to static electricity which can damage them. Unlike the optical media described above, flash drives can be damaged by liquids.
3
- Read-only
- Read-only media is prepared at the factory and cannot be altered by the consumer. The most prevalent examples of read-only memory today are the CD-ROM and the DVD.
- Write-once
- Write-once media is blank when purchased and is written by the consumer. Once it is written to, the data on it cannot be changed. An example of write-once media is the CDR (or CD-R).
- Write-rewrite
- Write-rewrite media can be written, erased, and rewritten by the end user. An example is the CD-RW. This type if media is generally more expensive than the CD, the DVD, or the CDR. In more modern times, the flash drive has taken the place of standard "Write-rewrite media.
4
- a. Processor speed
- b. Storage capacity of the hard drive
- c. Memory capacity (RAM)
Windows
Click the "Start" button. Then click "My Computer" with the right mouse button, and select "Properties". This will bring up a window. Select the "General" tab, and the computer will display the processor speed, memory capacity, as well as a number of other bits of information.
To find the storage capacity, click the "Start" button and then use the left mouse button to select "My Computer". This will open a new window which will show all the drives on the computer. Generally, the "C:" drive is the hard drive, so right-click on that and select "Properties" - this will show you the drive capacity as well as how much of the drive is in use.
Be sure to pay attention to the use of the left mouse button verses the right mouse button.
Mac
Click on the "Apple" at the top left corner of the screen. Now click on "About This Mac". This will bring up a window that contains the processor type and speed and how much memory the computer has. To find the storage capacity on the hard drive, click the "More Info..." button. Now click on "ATA" under "Hardware". There should be two "ATA Bus" sections. Click on the bottom section or the one that doesn't contain anything about a CD drive. The hard drive capacity is under "Capacity".
Linux
At the command prompt, type the following command:
cat /proc/cpuinfo
This will tell you the processor speed as well as the memory capacity. For the storage capacity, type:
df
This will yield an output similar to this:
Filesystem 1K-blocks Used Available Use% Mounted on /dev/hda2 20315844 7085116 12182088 37% / /dev/hda1 101086 11451 84416 12% /boot /dev/hda5 16674136 12303988 3523124 78% /home
This output above indicates that the computer has a single hard drive with three partitions. The first of these is the root partition which has a total capacity of 20 Gigabytes, the second is 101 Megabytes, and the third is 16.7 Gigabytes.
5
Increasing the processor speed of a computer will allow it to make more computations per second, thus improving its performance. Increasing the amount of RAM in a computer will also increase its performance, but for a different reason. When a computer program needs RAM, it requests it from the operating system (OS). If free memory is available, the OS assigns it to the program and all is well. If there is not enough memory to satisfy the request, the OS will copy the contents of some other program's RAM to the hard drive, and then give that to the requesting program. When the other program needs that memory again, the OS restores it from the hard drive (after writing the other program's version of the memory to the hard drive). This process is called "swapping," and it can really slow down a computer. However, all the programs continue to work as designed, and the computer makes maximum use of the resources available to it. Increasing RAM capacity will eliminate or reduce the amount of swapping that goes on.
Increasing the storage capacity of a computer will not make it run any faster (as increasing the processor speed and memory capacity will), but it will allow more files and programs to be stored on the computer.
6
Laser Printer
Adventist Youth Honors Answer Book/Computers/Laser printer
Ink Jet Printer
Adventist Youth Honors Answer Book/Computers/Ink jet printer
7
7a
An important fact about modern computing is that computers eventually fail. If the hard drive on a computer fails, it may be difficult or impossible to recover the data that is stored on it. Forward-thinking computer users keep all of their important personal files backed up on external media so that when the computer fails, they still have their data.
7b
It is not nearly as important to back up program files, because the program can be re-installed when the computer is repaired or replaced. However, re-installing every program that a computer user needs can be a time-consuming and frustrating process. If the whole system is backed up, it can be restored in short order.
7c
The A/C power that feeds most businesses and households is subject to all kinds of disturbances that can disrupt or damage a computer. Lightning strikes can induce large currents in powerlines, and these translate into "surge" voltages. The increased voltage can easily damage a computer. Most often, this affects its power supply module. A surge protector is designed to absorb these voltage surges, preventing damage to the computer.
7d
An unfortunate fact of modern life is that the world is filled with evil (or immature) people who think it great fun to destroy data on a stranger's computer. Some of these people are capable of "hacking" their way into computer systems and altering files - even taking complete control of the computer. The computer can then be used to launch attacks against other computers. Sometimes this is done in order to install malicious software designed to analyze keystrokes. When the program detects that someone is engaged in online banking activities or ordering merchandise with a credit card, it springs into action, gathering account numbers and passwords which are then passed to the programmer. Once hacking was confined to a small community of immature, thoughtless programmers looking for a thrill, but it is becoming more and more an activity conducted by organized crime and rouge governments.
Firewalls and antivirus software are designed to combat these operations, but in order to be effective, they must be installed and constantly updated.
8
This research should be performed by the person earning the honor, but we will provide a few names for plugging into a search engine:
Steve Wozniak and Steve Jobs are probably the most important people in the early history of personal computer hardware, as together, they formed Apple Computer which produced the first commercially viable home computer. Bill Gates and the company he founded (Microsoft) have had more influence on computer software than anyone else. Other people to know about include Brian Kernighan, Dennis Ritchie, Ken Thompson, Richard Stallman, Vint Cerf, and Linus Torvalds.
9
So then, each of us will give an account of himself to God. - Romans 14:12, NIV
My times are in your hands; deliver me from my enemies and from those who pursue me. - Psalm 14:12, NIV
Be very careful, then, how you live—not as unwise but as wise, making the most of every opportunity, because the days are evil. - Ephesians 5:15-16, NIV.
We are responsible for how we spend our time, and God expects us to use it in His service. Ecclesiastes 3:1-8 starts out
There is a time for everything, and a season for every activity under heaven: a time to be born and a time to die, a time to plant and a time to uproot - Ecclesiastes 3:1,2, NIV.
Likewise, there is a time to compute and a time to not compute. It is very easy to become addicted to computing, and as with all things, moderation is the key to temperance.
10
- a. What operating system does each use? What are some advantages of that OS?
- b. What compatibility issues do these two types of computers have in relation to data sharing and program installation?
- c. What type of industries / careers tend to use each type of computer system?
With the importance of computing in today's world, it is highly likely that you know someone who could be described as "a long-term computer user." Perhaps a staff member in your Pathfinder club fits this description. Invite this person to attend a meeting to have this discussion. It would be a good idea to provide this person with the questions ahead of time to provide ample opportunity for preparations.